2012-11-12 Mote Migration
The new remote access server is finally ready for general usage. This means everyone will have remote access to a system that has all the same software and settings as a department workstation. Fire up Racket and do your CMPU 101 homework, submit your CMPU 203 homework assignment, or just open up IDLE to work on your NLTK work, whatever you need.
This new server has a lot more memory, more processing power and has a NVIDIA Quadro 600 card for CUDA programming. All of the same instructions for VNC and SSH access apply, and down the road NX access will be opened up for slower connections and a more responsive experience. The new server address will be mote.cs.vassar.edu, but mote33.cs.vassar.edu will work as well livevnc.cs.vassar.edu.
The switch to the new server will start Monday, November 12th @ 10:30 . This means the current server (mote33) will be shut off at that time and the new server (mote) will take its place. The process should only take a couple minutes but everyone should assume that the service will be unavailable 10:30 - 11:00.
Things to know
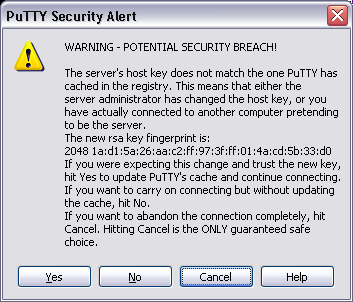
- The SSH protocol has changed enough and this is a different server so expect the new system to have different SSH host fingerprints. The new RSA fingerprint should be 9f:98:d5:06:14:59:7c:ce:75:4c:cf:81:12:ab:fd:7e.
The first time you connect, whether it is through PuTTY, a command line ssh client or any other SSH-based tool, you will get a message along the lines of “The server's host key does not match the one PuTTY has cached in the registry” or
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ @ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @ @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
or even
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ @ WARNING: POSSIBLE DNS SPOOFING DETECTED! @ @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
This is to be expected. Please follow the steps outline by your client to correct your registry of known host fingerprints. For PuTTY you just have to click Yes. For command line clients you will be told a line number to delete in your ~/.ssh/known_hosts file, or you can use the ssh-keygen tool with the -R option to remove the host fingerprint, such as ssh-keygen -R mote33.cs.vassar.edu.